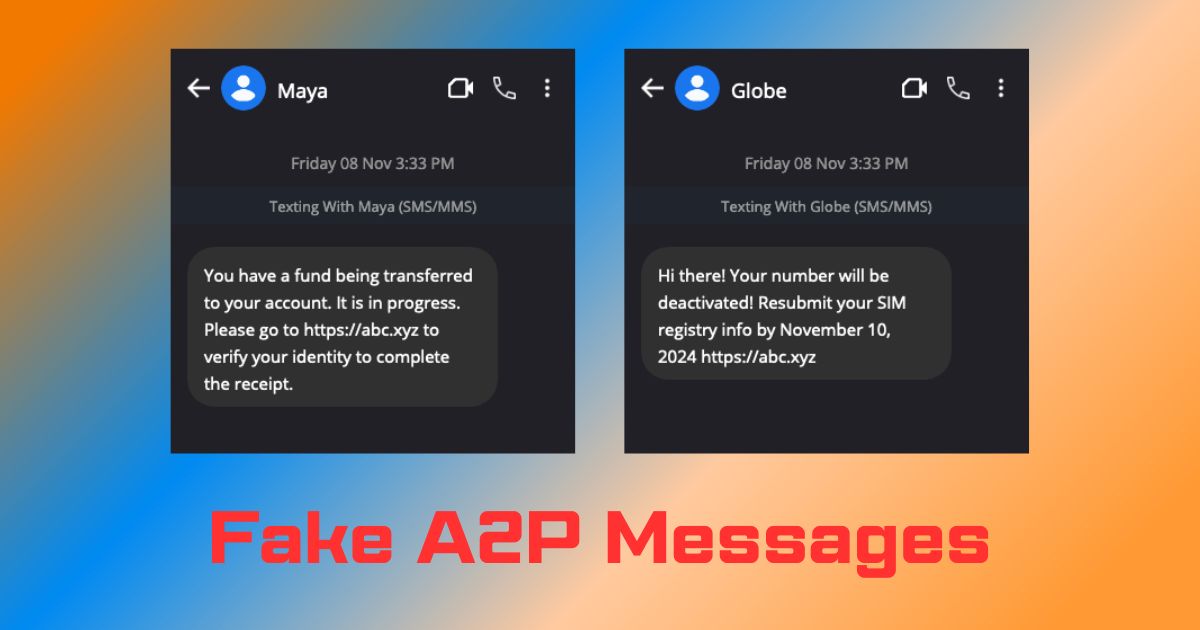
In recent months, a worrying increase in fake Application-to-Person (A2P) messages has emerged as a major concern, leading to a spike in phishing scams that target unsuspecting individuals here in the Philippines. A2P messaging, a common method used by businesses to communicate with customers, has now become a tool for scammers, who are exploiting it to trick recipients into divulging sensitive information, often resulting in severe financial and privacy consequences.
A2P messages are typically used by legitimate organizations to send automated notifications such as bank alerts, two-factor authentication (2FA) codes, appointment reminders, and marketing updates. However, fraudsters (bad actors) have found ways to imitate these messages, crafting them to closely resemble those sent by banks, retailers, and other service providers. By including familiar logos, phrasing, and even specific account details, these fake A2P messages appear trustworthy, which increases the likelihood of recipients falling victim to the scam.


A2P (Application-to-Person) messaging works through a streamlined process involving several key components to deliver automated messages directly to end users. First, an A2P platform, typically managed by a business or service provider, generates the message content — such as a bank alert, two-factor authentication code, or marketing update. This message is then sent through an SMS gateway, which serves as the intermediary system responsible for formatting and routing the message. The SMS gateway connects with mobile service providers to ensure that the message is delivered across various networks and reaches the intended recipient’s device. The mobile service provider finalizes the transmission, allowing the message to appear on the recipient’s phone as a regular SMS or notification. This multi-step system ensures that messages are efficiently routed and reliably delivered, making A2P a valuable tool for organizations to communicate directly with customers in real time.
Bad actors are increasingly turning to illegal devices, like SMS blasters, to send A2P-type messages that imitate legitimate notifications from banks, retailers, or other trusted sources. SMS blasters allow these actors to bypass regulated A2P channels and directly connect to mobile networks, sending bulk messages without oversight from mobile service providers or A2P platform providers. By using these devices, scammers can deliver high volumes of phishing messages or unauthorized marketing texts, often containing fraudulent links designed to steal personal or financial information. Unlike properly regulated A2P messages, these illegitimate messages evade the usual security filters, making them more likely to reach recipients. As a result, regulators are increasingly warning the public about these methods and urging caution, as spotting the difference between legitimate A2P notifications and these deceptive messages can be challenging.
The most common goal of these phishing scams is to steal personal information such as usernames, passwords, or bank and credit card details. Typically, the message contains a link that directs users to a fake website designed to look like a legitimate platform. Once there, users are prompted to enter their credentials or financial information, which is then collected by cybercriminals. Some messages even go a step further, enticing users with offers of fake rewards or threatening account suspension to increase urgency and encourage hasty, uninformed actions.

Cybersecurity experts (the real ones and not the charlatans) warn that fake A2P messages pose a particularly high risk due to their effectiveness in bypassing traditional security measures, such as email spam filters, and reaching individuals directly via their mobile devices. This direct access to users’ phones, coupled with the inherent trust users place in A2P messages, makes these phishing attempts especially successful.
How to Spot Fake A2P Messages?
To protect against these scams, it is recommend that users remain vigilant when receiving messages, especially those containing links or requests for personal information. Users should verify the authenticity of any communication by contacting the company directly and avoid clicking on links embedded in unsolicited messages. In addition, regularly updating software, enabling multi-factor authentication, and using security tools to filter out known phishing messages can help safeguard against these scams.
Spotting fake A2P messages requires a keen eye for details that seem out of place. One key indicator of a fraudulent message is the inclusion of clickable links, especially those claiming to resolve urgent issues or offer rewards. The Bangko Sentral ng Pilipinas (BSP) has made it clear that BSP-supervised financial institutions will never send messages with clickable links, as this is a common tactic used by scammers to lure users to malicious websites. Legitimate institutions will always direct customers to use official channels, such as banking apps or websites, without linking directly in a message. Fake messages often have subtle spelling errors, generic greetings, or unusual sender IDs. If a message urges immediate action or requests sensitive information like account numbers or passwords, it’s best to verify directly with the company before taking any steps.
With the rise of fake A2P messages showing no signs of slowing down, awareness and caution are essential to avoid falling victim to these sophisticated phishing schemes. By understanding the tactics used by scammers and taking proactive security measures, users can better protect themselves in an increasingly vulnerable digital landscape.