Palo Alto Network‘s in-house threat research team, Unit 42, analyzed data from a variety of public data sources around the globe and came up with conclusions about the growing threats the software supply chains of organizations face on a daily basis. Their findings indicate that many organizations may have a false sense of security in the cloud and in reality, are vastly unprepared for the threats they face.
The recent software supply chain attacks such as SolarWinds and Kaseya have shed a glaring light on the disparity between organizations’ perceptions of security within their cloud infrastructure, and the reality of threats in their supply chains that can impact business catastrophically. In the latest edition of Palo Alto Networks’ Unit 42 Cloud Threat Report, 2H 2021, Unit 42 researchers dive deep into the full scope of supply chain attacks in the cloud and explain often misunderstood details about how they occur. They also provide actionable recommendations any organization can adopt immediately to begin protecting their software supply chains in the cloud.
In addition to analyzing data, Unit 42 researchers were commissioned by a large SaaS provider (a Palo Alto Networks customer) to run a red team exercise against their software development environment. In just three (03) days, a single Unit 42 researcher discovered critical software development flaws that left the customer vulnerable to an attack similar to that of SolarWinds and Kaseya.
“The cloud is at the center of what executives and technology leaders were discussing during last October’s Cybersecurity Month. Many of them were saying that the cloud is a critical component of their digital transformation initiative or strategy, as part of an overall business strategy. In the Philippines, the cloud is going mainstream,” according to Oscar Visaya, Philippine Country Manager of Palo Alto Networks during a virtual press briefing this week.
Key Research Findings
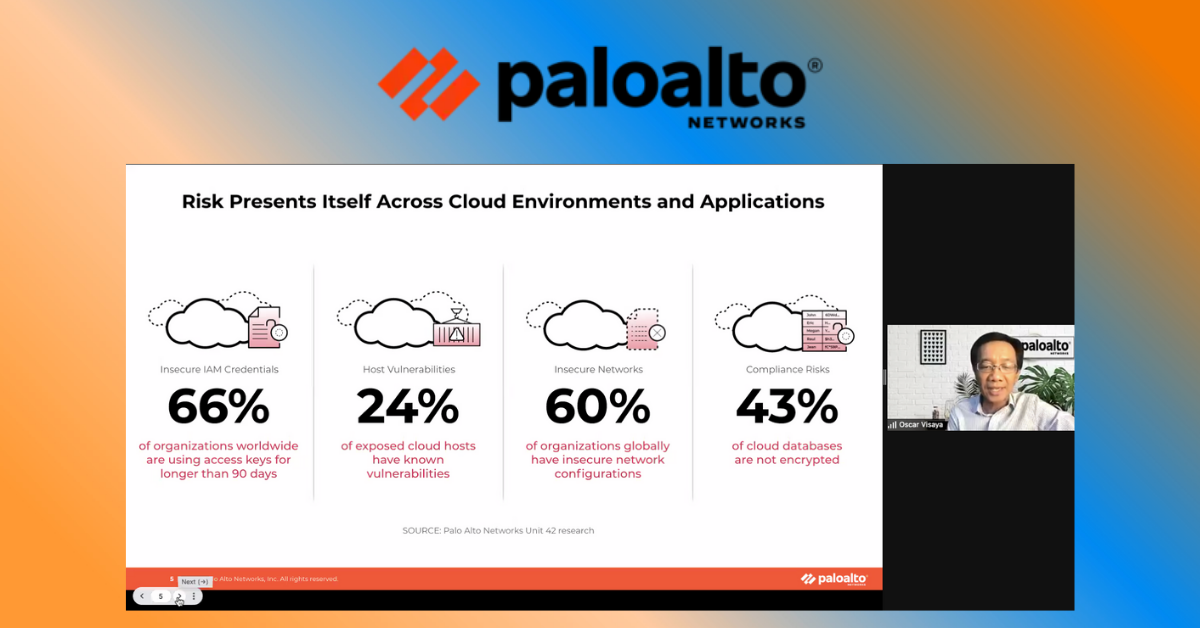
The large SaaS provider detailed in the red team exercise has what many would consider a mature cloud security posture. However, during the exercise, Unit 42 researchers were able to leverage misconfigurations in the organization’s software development environment, such as the presence of hardcoded IAM key pairs, which would have allowed them to control all development processes and thus conduct a successful supply chain attack.
Unit 42 researchers also found that 21% of the security scans they ran against the customer’s development environment resulted in misconfigurations or vulnerabilities, highlighting how process gaps and critical security flaws leave an organization exposed and susceptible to a business-halting attack.
The research also discovered that 63% of third-party code templates used in building cloud infrastructure contained insecure configurations, and 96% of third-party container applications deployed in cloud infrastructure contain known vulnerabilities. With this level of risk, an attacker could easily gain access to sensitive data in the cloud and even take control of an organization’s software development environment.
Based on the Unit 42 team’s findings, it’s evident that unvetted code can quickly snowball into a security breach, especially as infrastructure flaws can directly impact thousands of cloud workloads. For that reason, it is critical that organizations understand where their code is coming from since third-party code can come from anyone, including an Advanced Persistent Threat (APT).
Teams continue to neglect DevOps security, due in part to lack of attention to supply chain threats. Cloud-native applications have a long chain of dependencies, and those links have relationships of their own. DevOps and Security teams need to gain visibility into the bill of materials in every cloud workload in order to evaluate risk at every stage of the dependency chain and establish guardrails.
Palo Alto Networks is the global cybersecurity leader shaping the cloud-centric future with technology that is transforming the way people and organizations operate.